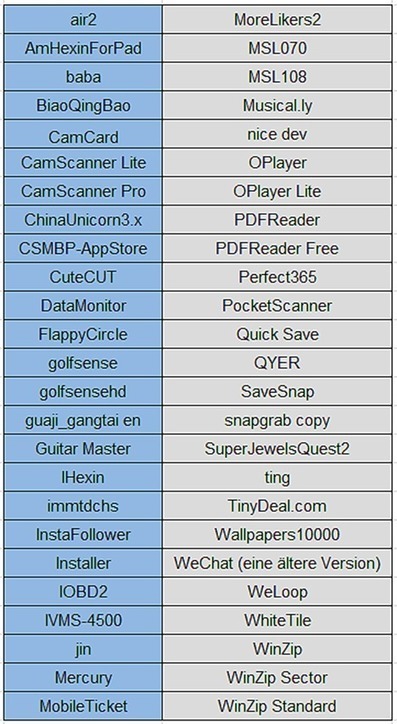
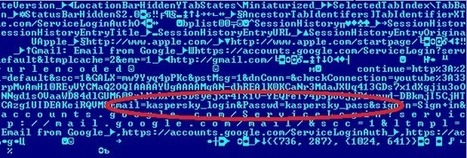
Apple hat bekanntgegeben, dass der hauseigene App Store erfolgreich von Hackern angegriffen wurde. Im Rahmen des Angriffs wurden hunderte Apps mit schädlichem Code infiziert, die anschließend zum Download bereitstanden.
Learn more / En savoir plus / Mehr erfahren:
.
http://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security
.
.
Via Gust MEES



 Your new post is loading...
Your new post is loading...






Learn more / En savoir plus / Mehr erfahren:
.
http://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security
.
https://gustmees.wordpress.com/2014/03/05/often-asked-questions-are-there-cyber-security-dangers-with-apps-and-whats-about-privacy/
.
http://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security/?tag=XcodeGhost+malware+sneaks+into+the+App+Store...