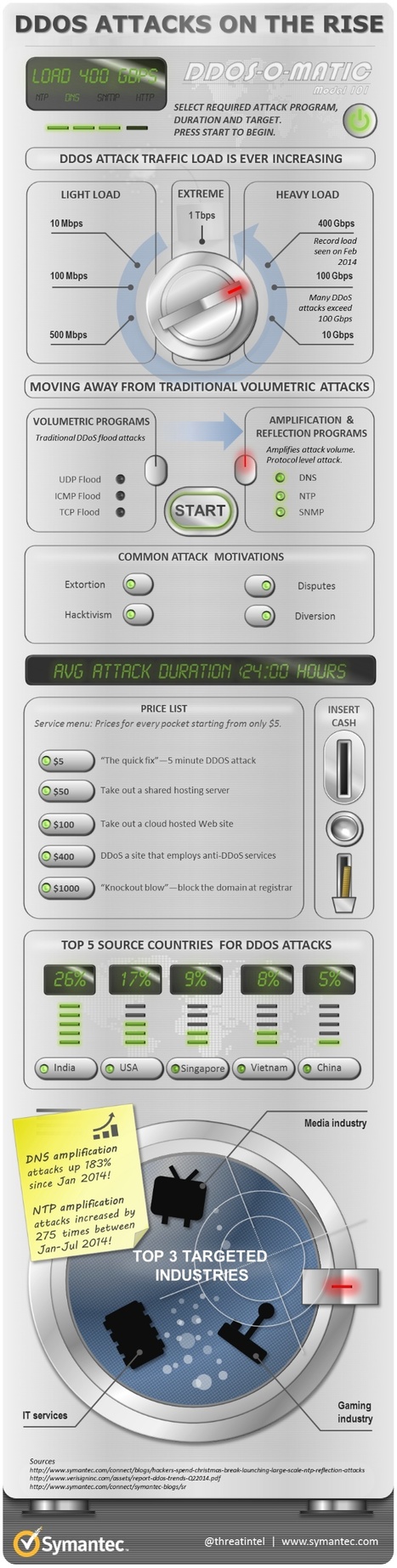
Research and publish the best content.
Get Started for FREE
Sign up with Facebook Sign up with X
I don't have a Facebook or a X account
Already have an account: Login

 Your new post is loading... Your new post is loading...
 Your new post is loading... Your new post is loading...

Gust MEES's curator insight,
March 11, 2014 10:42 AM

Gust MEES's curator insight,
March 11, 2014 10:47 AM

Gust MEES's curator insight,
March 11, 2014 10:48 AM
|
|







Learn more:
- http://www.scoop.it/t/securite-pc-et-internet/?tag=DDos
- http://gustmees.wordpress.com/2014/02/15/often-asked-questions-who-are-the-countries-with-most-hosted-malware-servers-and-other-cyber-problems/
- http://gustmees.wordpress.com/2013/05/13/visual-cyber-security-see-attacks-on-real-time/